Tech support scams: they’re an ugly reality of the Internet and they’ll never go away because people fall victim to them every single day! They are virtually free ATM’s for hackers! Knowing how to identify these tech support scams, how to stay proactive, and what to do if you have already fallen prey are the only real ways to vigilantly deal with them.
Spot the Problem
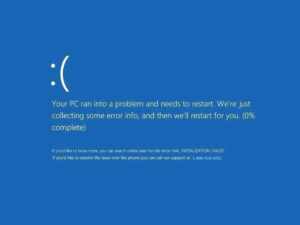
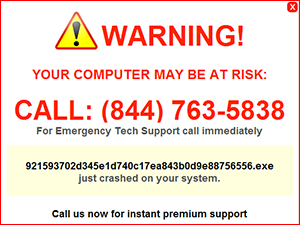
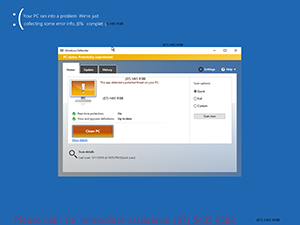
Tech support scams come in all shapes and sizes. Knowing what you’re up against is half the battle. Hackers will send fake tech support pop-up’s fashioned to look like legitimate alerts from companies like Microsoft, Apple, and more. Most times these hackers will tell users that their Windows computer or Apple Mac OS is infected, and provide a tech support number for help. These are known as Call for Support Scams and are never real. Alerts will often appear as below:
Most of these tech support scams rely on social engineering to trick your brain into believing they are legitimate. They will oftentimes include the following to prove their legitimacy:
- Force pop-up image onto your browser on full-screen
- Disable your task manager
- Continuously display pop-up windows
- Play audio messages
The end goal is to always force the user into calling the fake tech support number provided. Do not be fooled. These fake tech support pages are always fake and always malicious websites in disguise. If the user does call the number, “support” will always follow anything up with an attempt to extract money from the user for malware removal services. This should be the biggest red flag.
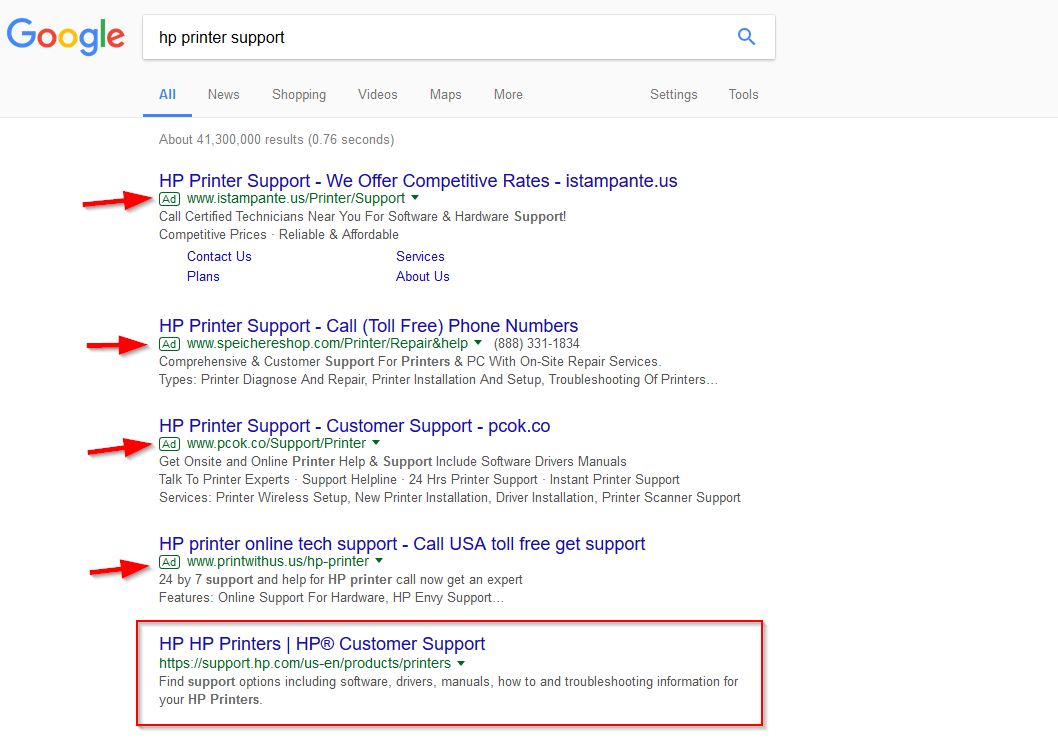
Furthermore these scammers often purchase Google search results, so searching for “Gmail help” or “HP Printer Support” will likely yield these scammers in the top search results. In the example below the first FOUR results are AD’s for scammers! Do not search for solutions yourself unless you are confident you can tell the difference between AD’s in the results and real links. It is always best to contact us for support!
Be on the Look Out For
When trying to assess authentic alerts from counterfeit claims, always bear in mind that Microsoft, Apple, or any other major tech company will never provide a technical support number. Furthermore, they will never ask for payment over the phone for a technical support problem. Be cautious of several other red flags, such as:
- Being asked for remote access to your computer. Most likely, this is a way for the hacker to install malware on your computer that gives them access to sensitive data,like usernames and passwords.
- Being sold additional software. This is also a means to install malware and extract further payment from you.
- Being asked for credit card information for billing.
- Being directed to a website that requests personal information such as credit card info, social security, etc.
How to Protect Yourself
If you’re targeted by any number of tech support scams, you should always employ the following methods:
- If you see any type of pop-up message pushing you to dial into tech support, DO NOT call.
- Pop-ups should never prompt a call in number.
- Pop-ups usually only contain important security updates for your computer, never numbers to call or areas to insert personal data.
- Specifically, Microsoft has stated that they will NEVER reach out to provided unsolicited PC or technical support.
- If someone calls you claiming to be tech support, DO NOT take their call. Scammers can create fake caller ID’s, so be wary of who you’re talking to.
- If you are concerned about a pop-up or message on your screen, call your IT or security providers directly with the numbers you have saved on file.
- DO NOT allow anyone who you do not know to access and take control of your computer ever.
- Share this information with all staff members in your business
If you’re targeted specifically by Microsoft scam support, you should always be aware of the following:
- Microsoft has stated that they will NEVER reach out to provided unsolicited PC or technical support.
- Microsoft’s error and warning messages NEVER include a phone number.
- Never grant access to your laptop/PC/digital device unless directed by your trusted IT provider
- If you’re unsure, take down the caller’s personal information and report it to your IT provider
- Share this information with all staff members in your business